When we think about the minimum amount of information required to “onboard” a customer, it’s often the email address and mobile number that first come to mind. This information alone enables personalised communication and provides a foundation from which brand-customer relationships can be built or destroyed. A brand’s coveted ‘email subscriber count’ metric probably gets more attention than it deserves, but there’s no doubt it can be used (or abused) to drive sales today.
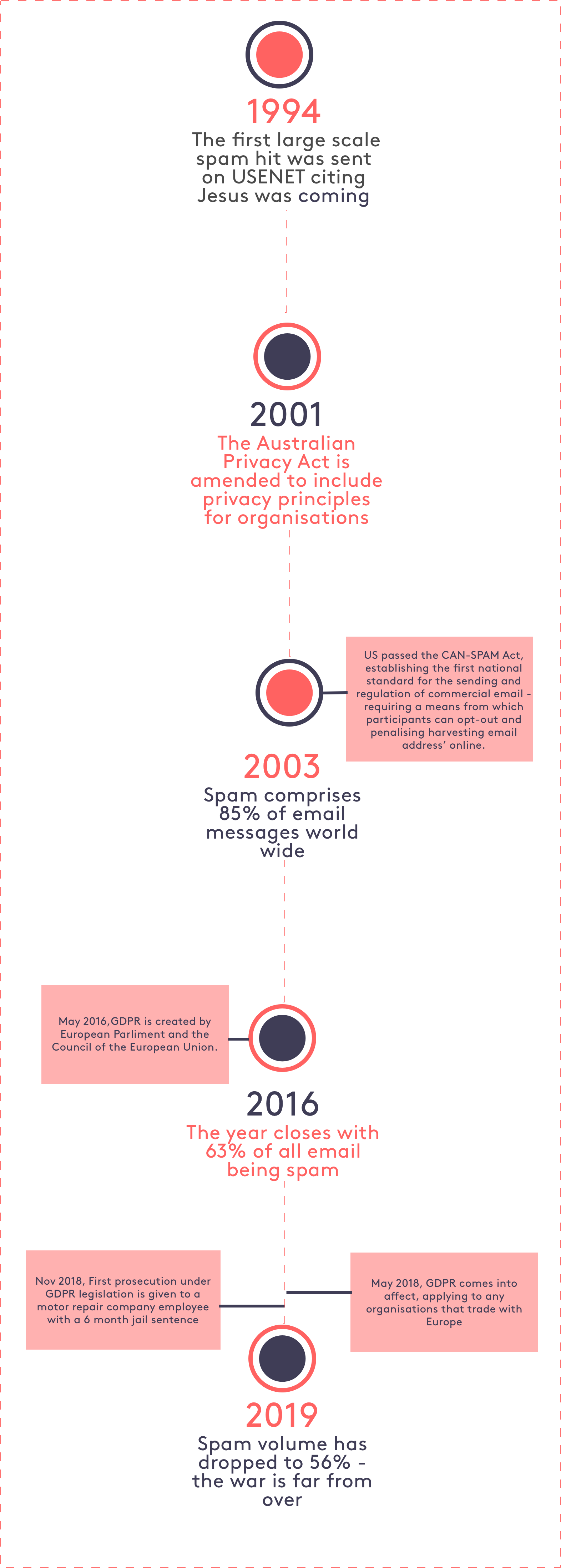
It’s no surprise then that the requirement to treat these two fields with the utmost level of respect is non-negotiable. Misuse of this information, in one form or another, has played midwife globally to regulations like the GDPR in Europe, the Australian Privacy Principles and the USA's CAN-SPAM Act.
These rules are in place to protect us from the brands that sneak us into mailing lists without explicit or consensual processes - you know the ones? With third party tricks or list buying tactics? For brands who have customers at the centre of their profile creation process, participation is a privilege, not an obligation.
A Brief History on the War Against Spam
The Recruits
Those who invest in CX and Omneo, join the ranks in a fight against the malpractice, and they’re not alone. The tactical efforts outlined below give us a sense of what navigating the world of customer-centric engagement looks like today.
Machine Learning
Email providers such as Gmail, Yahoo mail and Outlook have employed the combination of different machine learning (ML) techniques such as Artificial Neural Networks in their spam filters. ML can adapt to varying conditions, Gmail and Yahoo mail spam filters do more than just checking junk emails using pre-existing rules. They generate new rules themselves based on what they have learnt as they continue in their spam filtering operation (Dada et al, 2019)
Number blocking features for mobiles
Marking text messages as ‘spam’ is now easier than ever with Android and iOS employing their own methods for user elected blocking. Also enabling the ability to report senders to manufacturers, related carriers, and local regulators and watchdogs.
Domain-based Message Authentication
Generally employed by organisations, DMARC is a protocol that uses a series of technical checks to determine the legitimacy of an email sender. Read about how it works in plain English here. Failing DMARC compliance often results in a lengthy review process or sender rejection. DKIM and SPF. are also important configurations on your domain that must not be skipped.
Blacklisting
Internet Service Providers combat spam by implementing tools to process and filter incoming email determining whether or not they can be trusted. These providers monitor IPs and domains for those actively sending emails. Compiling a blacklist and logging if a sender is receiving positive or negative reactions from the recipient. If adverse reactions are prominent, senders are then placed on the list and blocked from sending communications.
Want to learn more? Checkout DKIM and SPF.
What does this mean for Customer Onboarding and relationships? We know that customers appreciate personalised communication but brands mustn’t overstep their bounds, as the consequences of doing so are often permanent.
An Arsenal in Best Practice
In the relationship between customer and brand, spam isn't a one-way street. For customers, its unwanted communications in their inbox or phone. For business, its unverified or inaccurate data stored against customer profiles, that becomes more of a liability than an asset. So, what are the rules of engagement?
When collecting mobile numbers:
-
Check for a valid mobile pattern or syntax for a particular country
-
Check if the mobile already exists within your customer base, and if so, provide a secure login to proceed to that profile instead rather than creating a duplicate - via email or SMS
-
Employ a paid validation service which can check the number against a known number registry and return either - Valid, inValid, or ‘cannot validate’ (which means maybe yes maybe no, we can’t tell)
-
Send a link to that mobile number to allow the customer to self validate via a click or entering a code
When collecting email addresses:
-
Check for a valid email pattern or syntax (with @ and . and no spaces or special characters
-
Check if the email already exists and if so provide a secure login to proceed further
-
Check that it has no common typos - eg “gamil” instead of “gmail” and suggest ‘did you mean gmail?’
-
Employ a paid validation service which can check the email address against a known number registry and return either - Valid, inValid, or ‘cannot validate’ (which means maybe yes maybe no, we can’t tell)
-
Send a link to that email address to allow the customer to self validate via a click or entering a code
- Be careful when asking a customer to enter someone else’s email address, ie with a referral program, as this does not give you permission to start talking to that customer directly unless handled correctly
For communications
Any commercial electronic messaging should follow these checklist principles:
|
Permission - messages can only be sent with the permission of the person who owns the account for the address (usually the recipient). This permission can be
|
|
|
Identification - messages must contain the name and contact details of the person or business that authorised the message (sender identification). |
|
|
Easy Opt Out- messages must contain a low (or no-cost) way for the recipient to stop getting all or some of the messages they are receiving (to ‘opt-out’ or unsubscribe). |
|
| Only use the contact method the way you outlined you would in initial onboarding | |
|
Don't share customer information without the explicit permission of the customer or to facilitate the processing of their data within the scope of your relationship with the customer |
|
| |
Be clear on the definitions of ‘personally identifiable’ and ‘sensitive’ information and only ask for what you need to serve the customer now or in the future. |
| |
In SMS messaging, only ask for YES/NO replies |
| |
If you're asking a customer to do something somewhere don't make them jump through hoops, direct them to promised destination upfront (See Profile Portal) |
| |
Be clear on what benefit/value you're providing the customer for each piece of communication. Pass communications through a lens of: Is it helpful? Is it personalised? Is it contextually relevant to the individual? |
| |
Understand engagement metrics, get feedback (read about how here), test and change! |
Have questions about how to design the customer onboarding flow? Revisit our foundations of customer onboarding or get in touch.
Resources: